How To Decrypt A Message
In many contexts the word encryption also implicitly refers to the reverse process decryption eg.
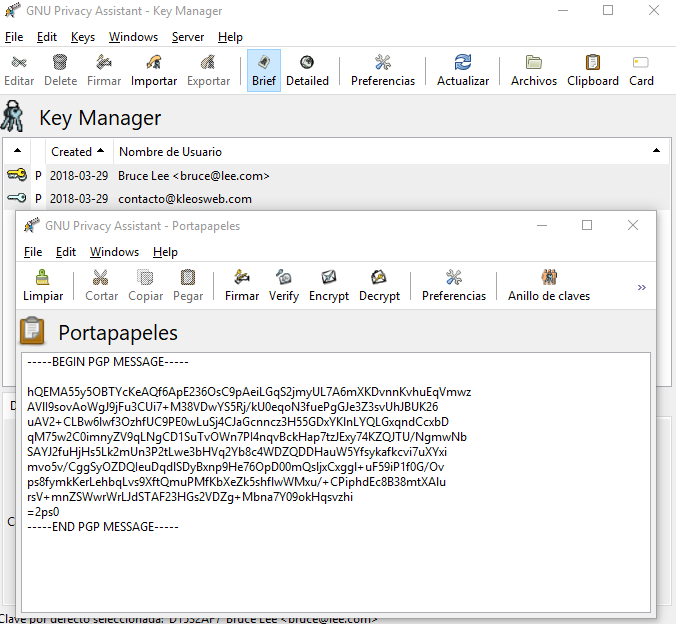
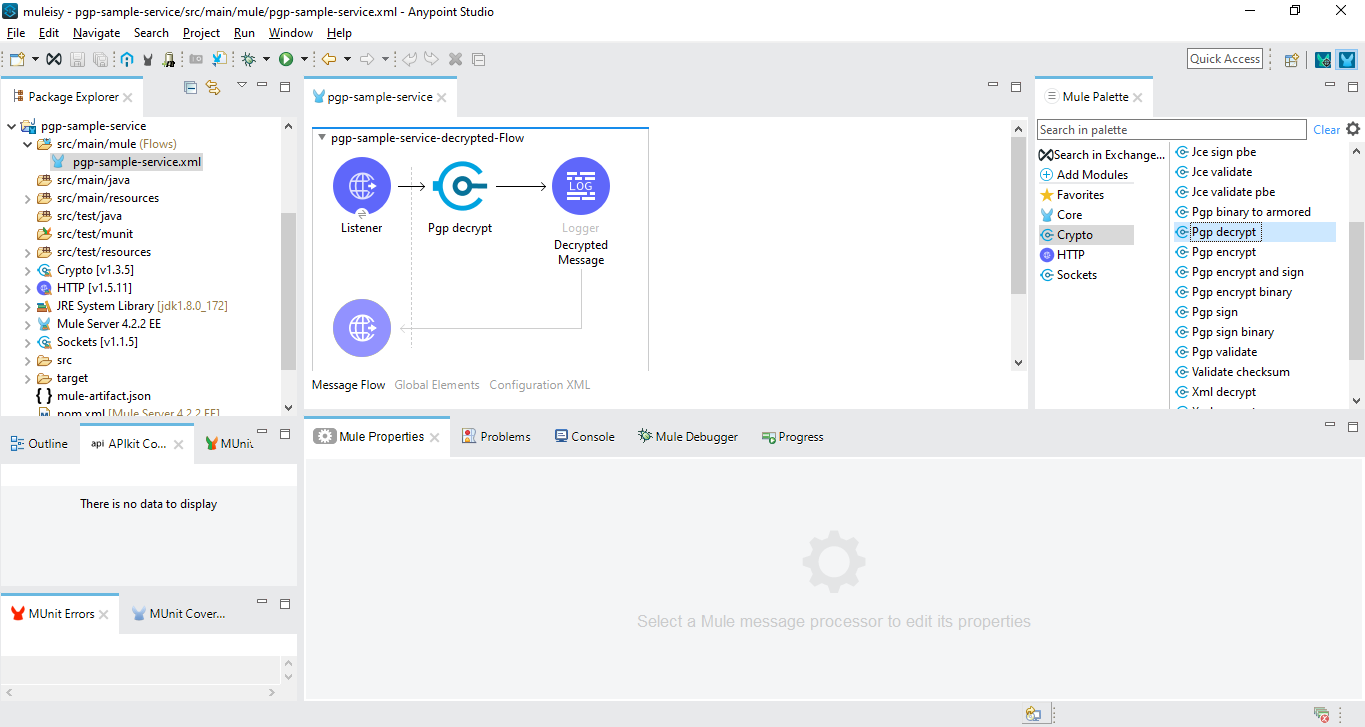
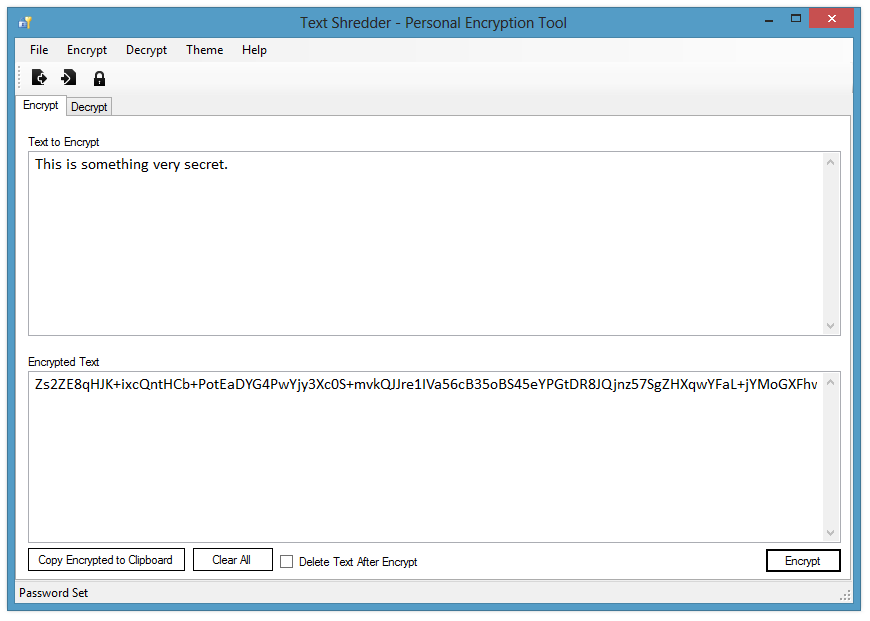
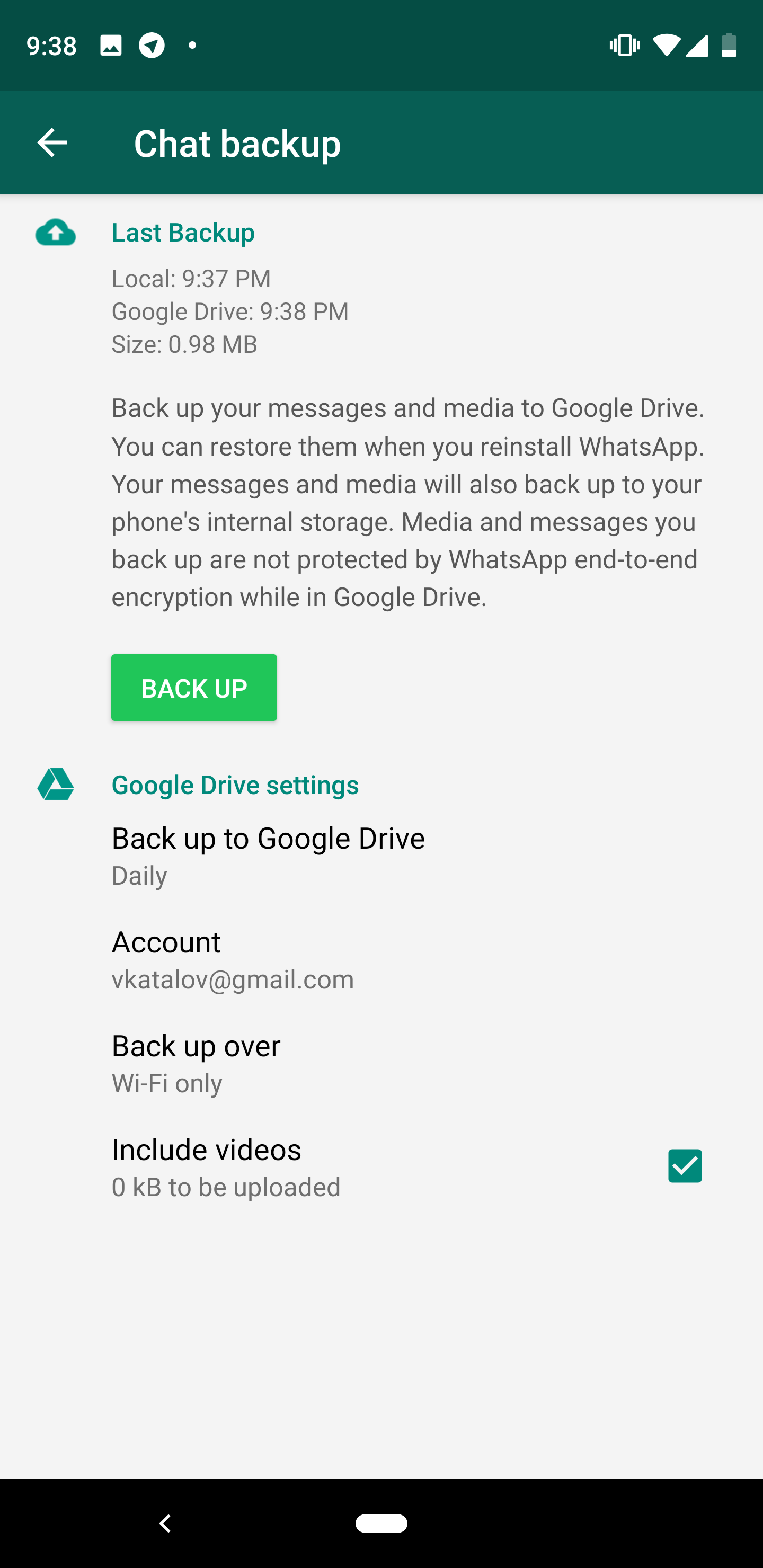
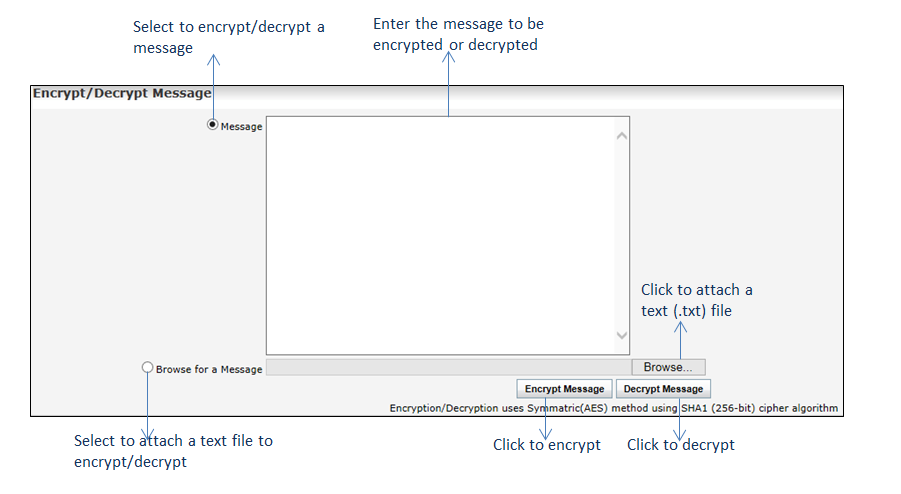
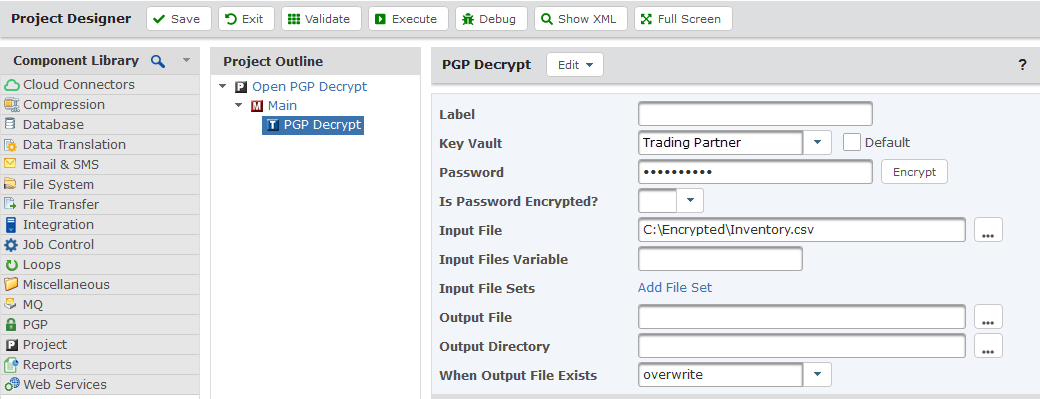
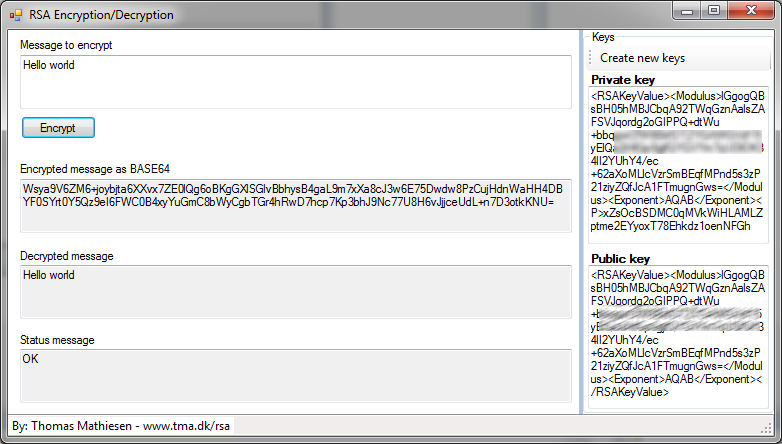
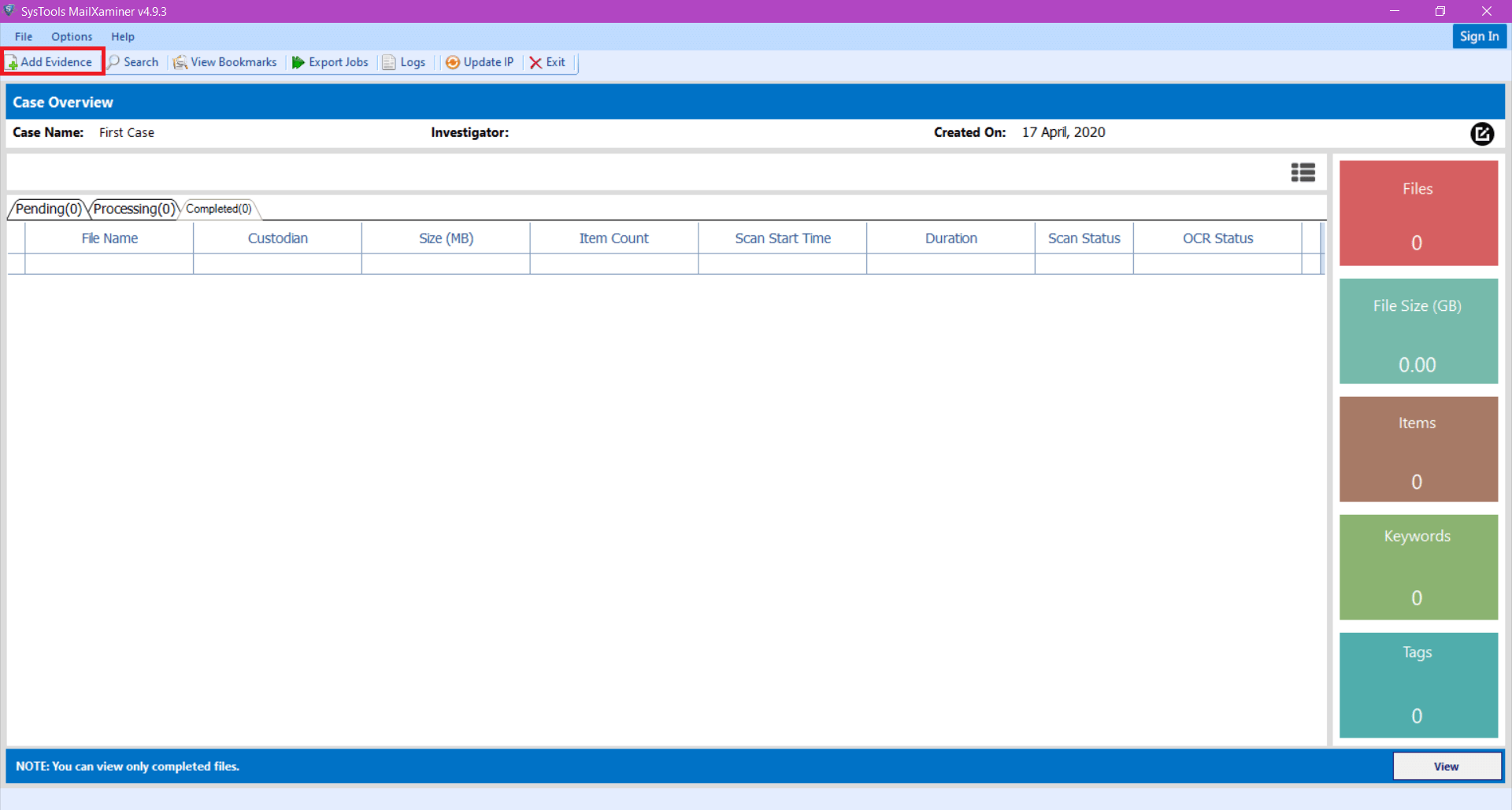
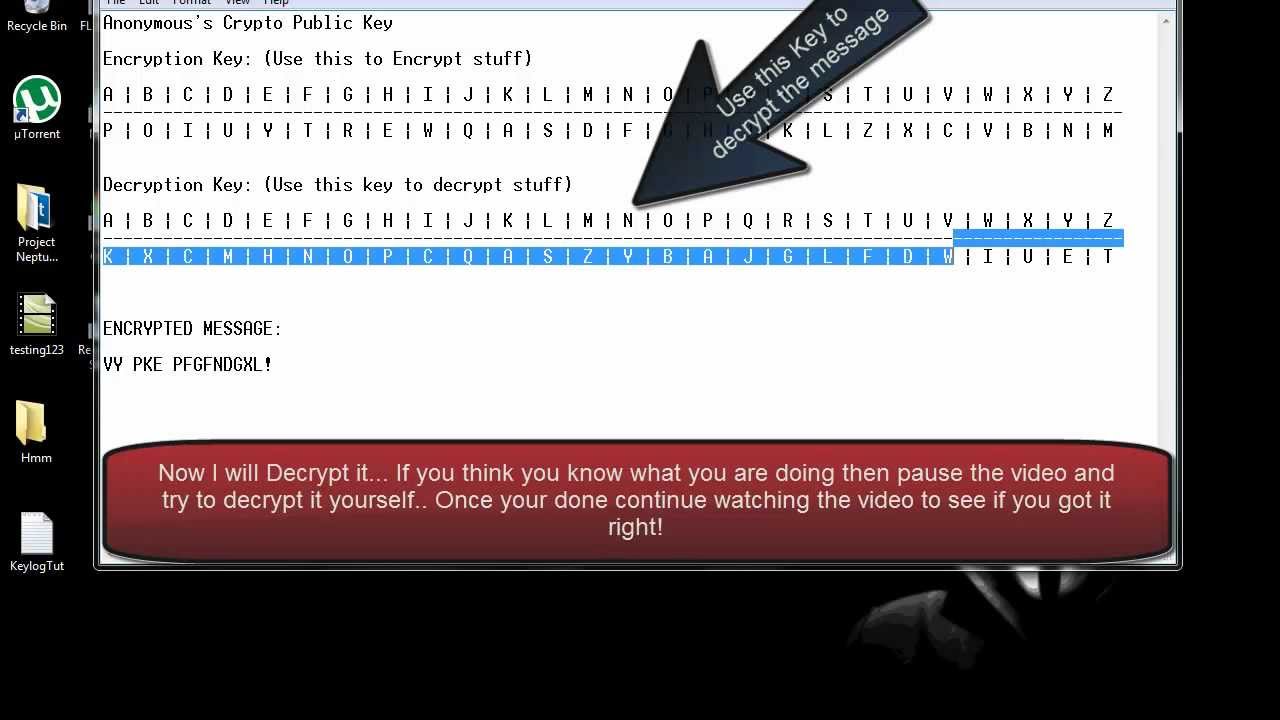
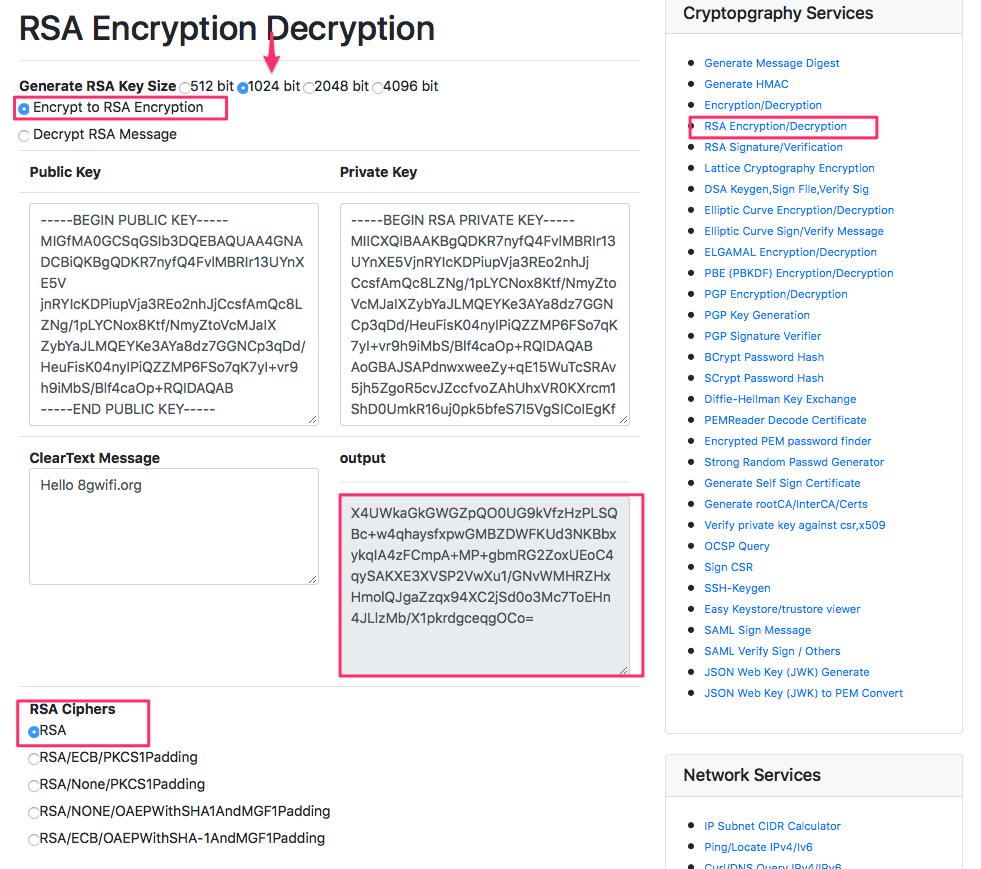
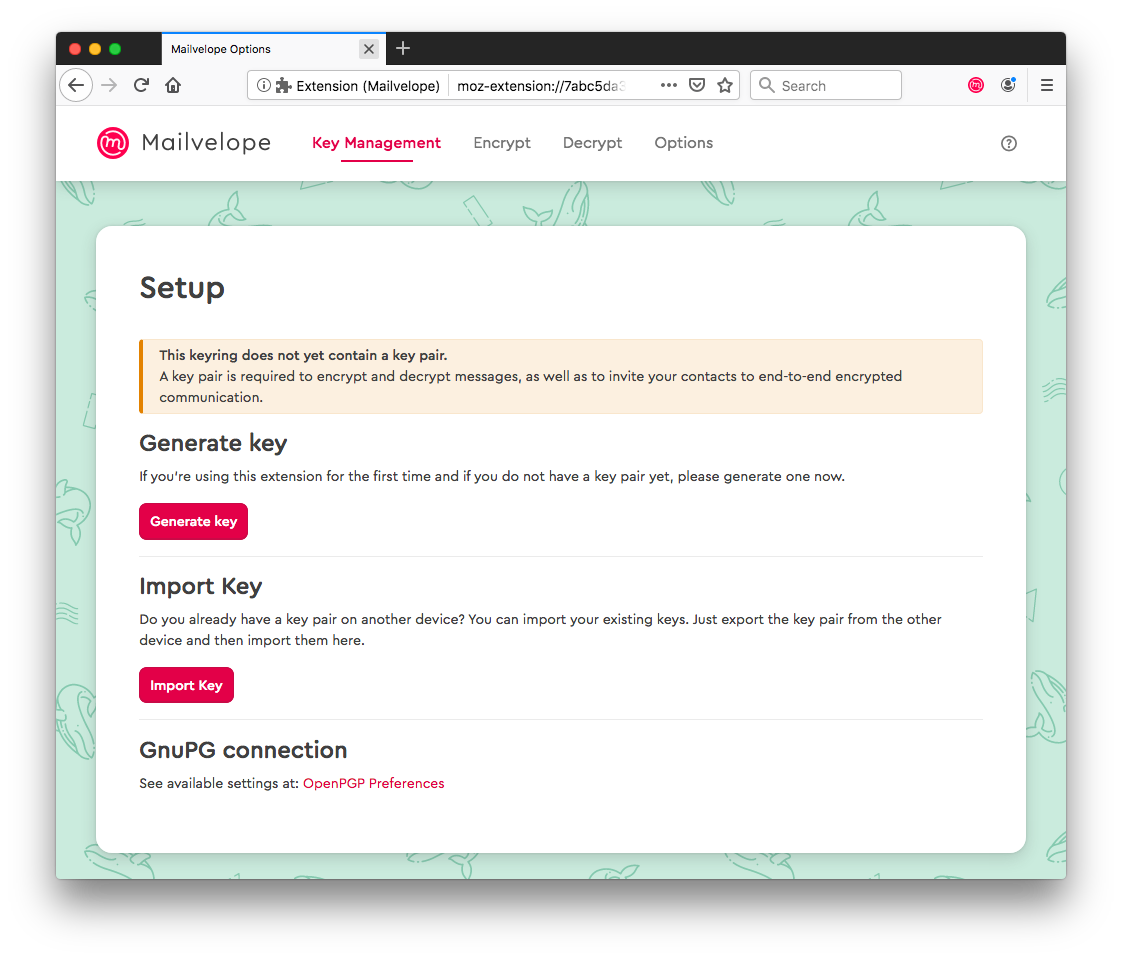
How to decrypt a message. We will encode the message using the public key and then decrypt it using the private key to get the original data back. We need to generate a public private keypair for us to encode and decode the message. Type your text in the text area and click on encrypt.
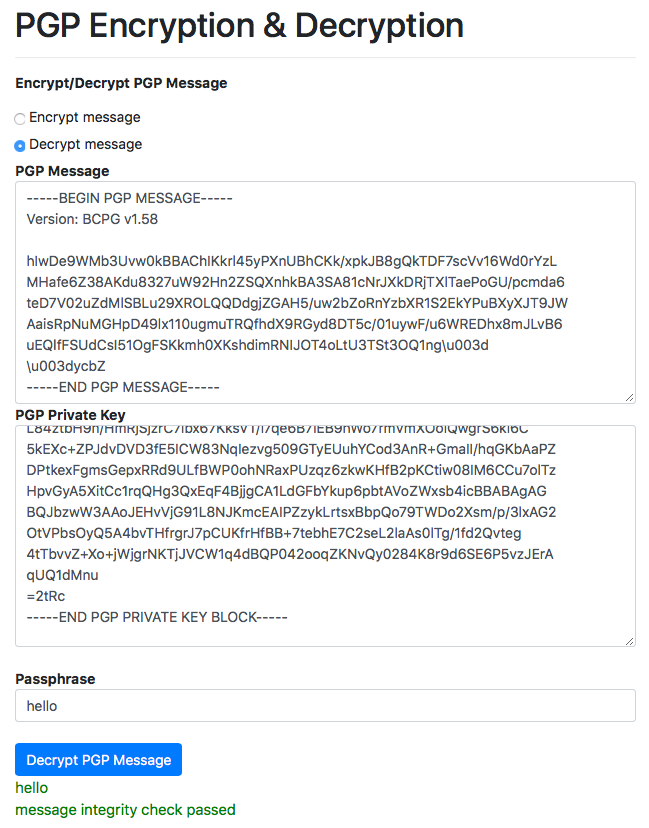
In this shift method you shift the entire alphabet a certain number of places in one direction. Lime 3 x research sourcestep 3 write down your message without spaces. If you supply the proper prp private key and passphrasepassword then you will be able to read the decrypted message otherwise you will see an error message the tool is unable to decrypt the message.
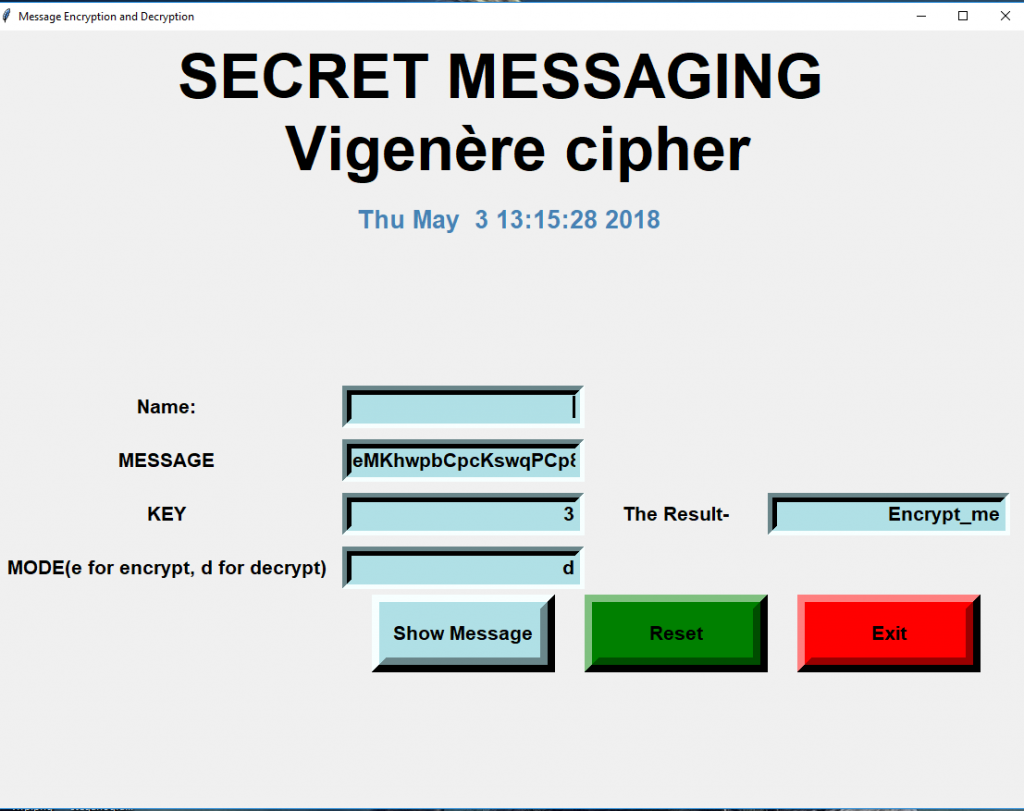
Private key is hidden from being displayed here. The decrypted text will be placed in the plain text box above. 2 x research sourcestep 2 think of a keyword that is shorter than the phrase or phrases you want to encipher.
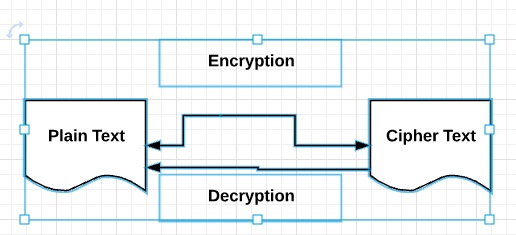
In other words a shift of three spaces left would replace the letter a with d b with e etc. Remember well that when encrypting a message if it is placed sign the recipient of the same must have us on your public keychain because otherwise it will be impossible to recognize our signature and the message will not be able to decode it. The result of the process is encrypted information in cryptography referred to as ciphertext.
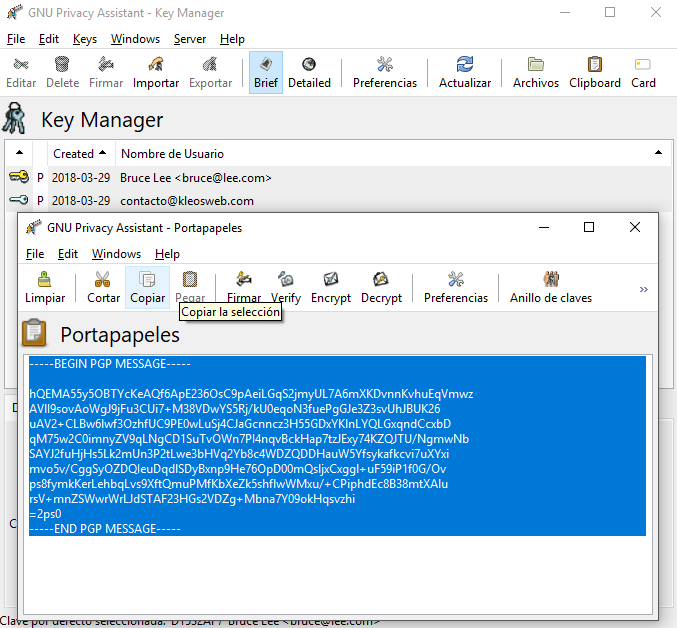
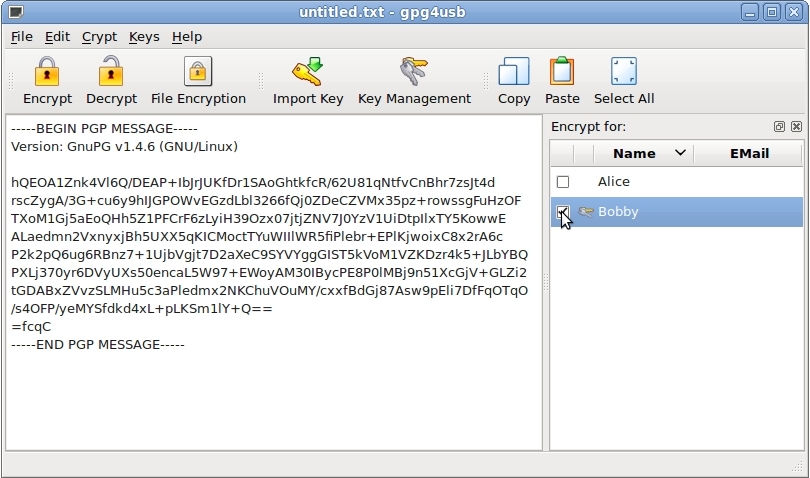
Next type cmd in the start menu that appears and then the enter key. Use the form below to generate your public and private keys. Then choose the pgp public key of the person whom you wish to send this message note that only that person will be able to decrypt this message.
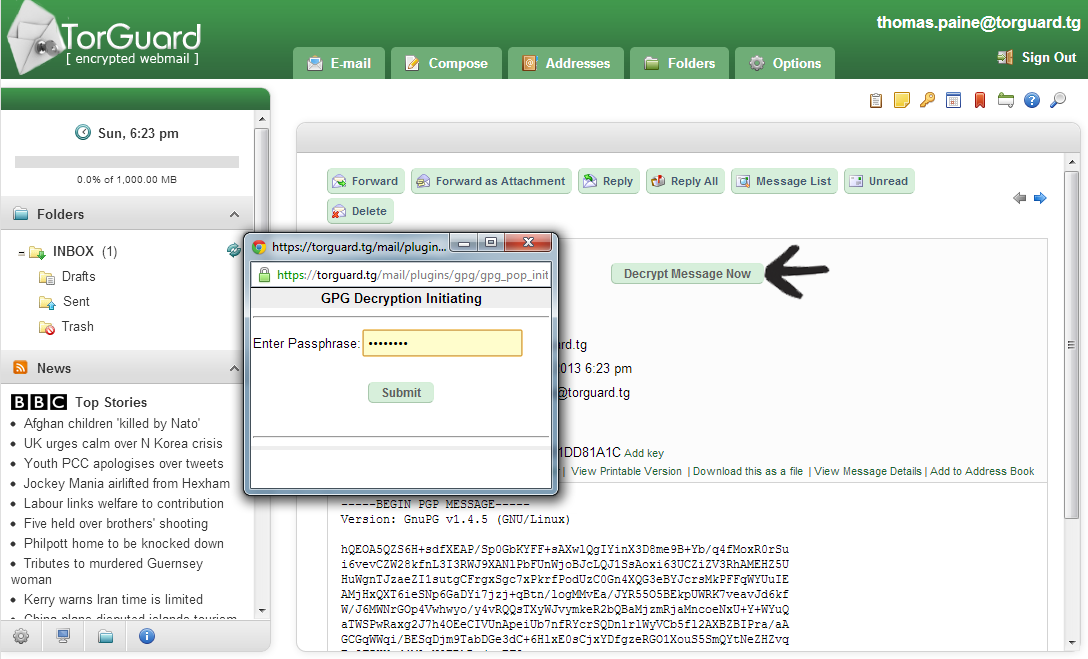
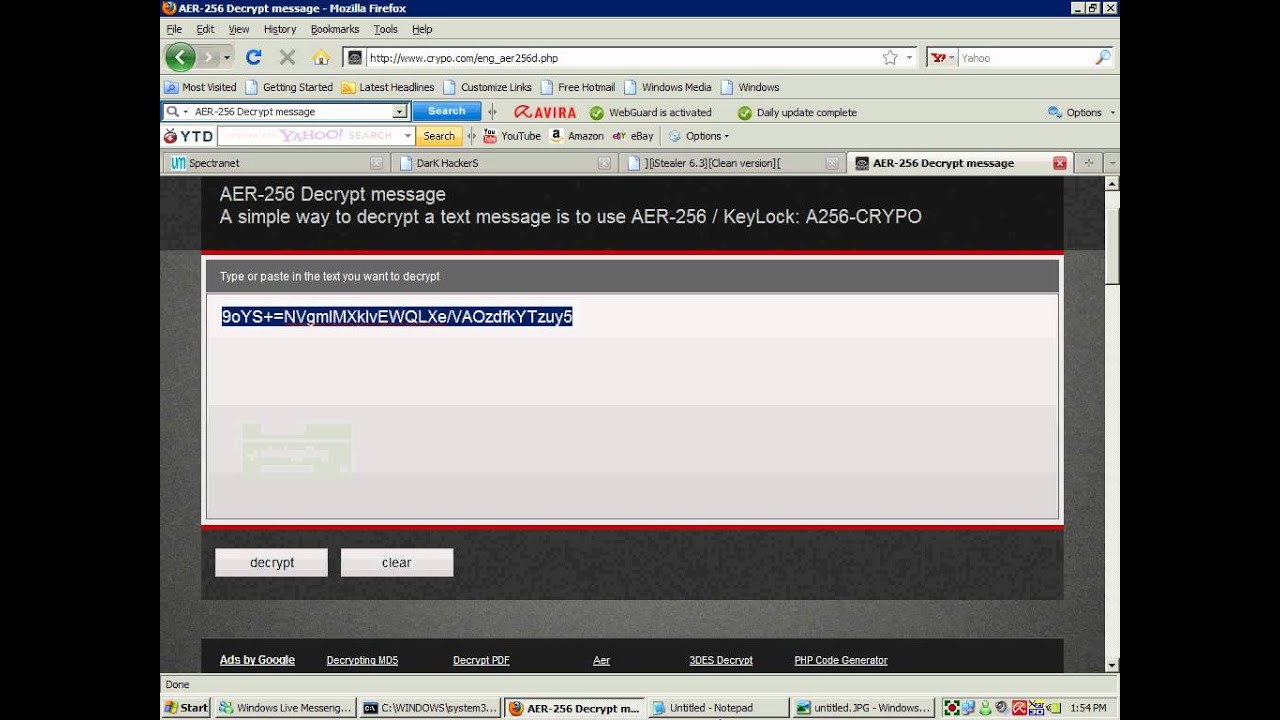
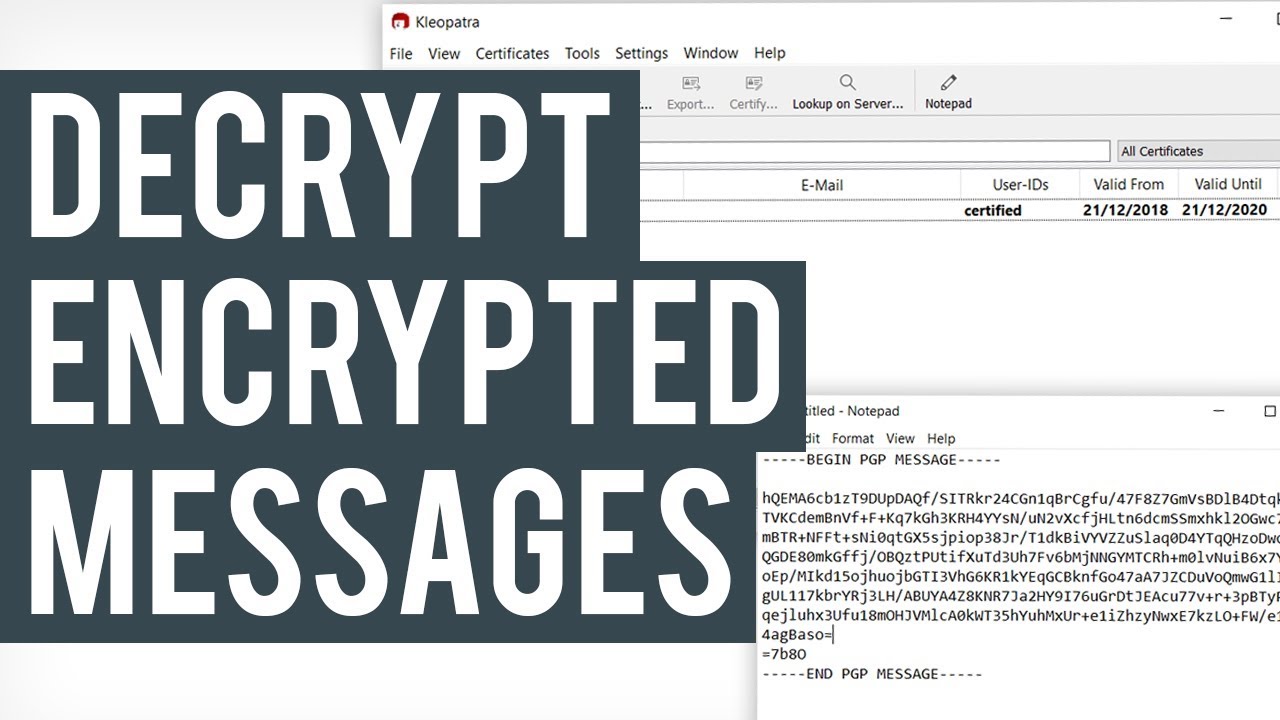
Text before and after the encrypted message is ignored and the encoding used by the message is determined automatically. This tool is simple to use. Enter your private pgp key your pgp passphrase and the pgp encrypted message you wish to decrypt then click on the decrypt message button.
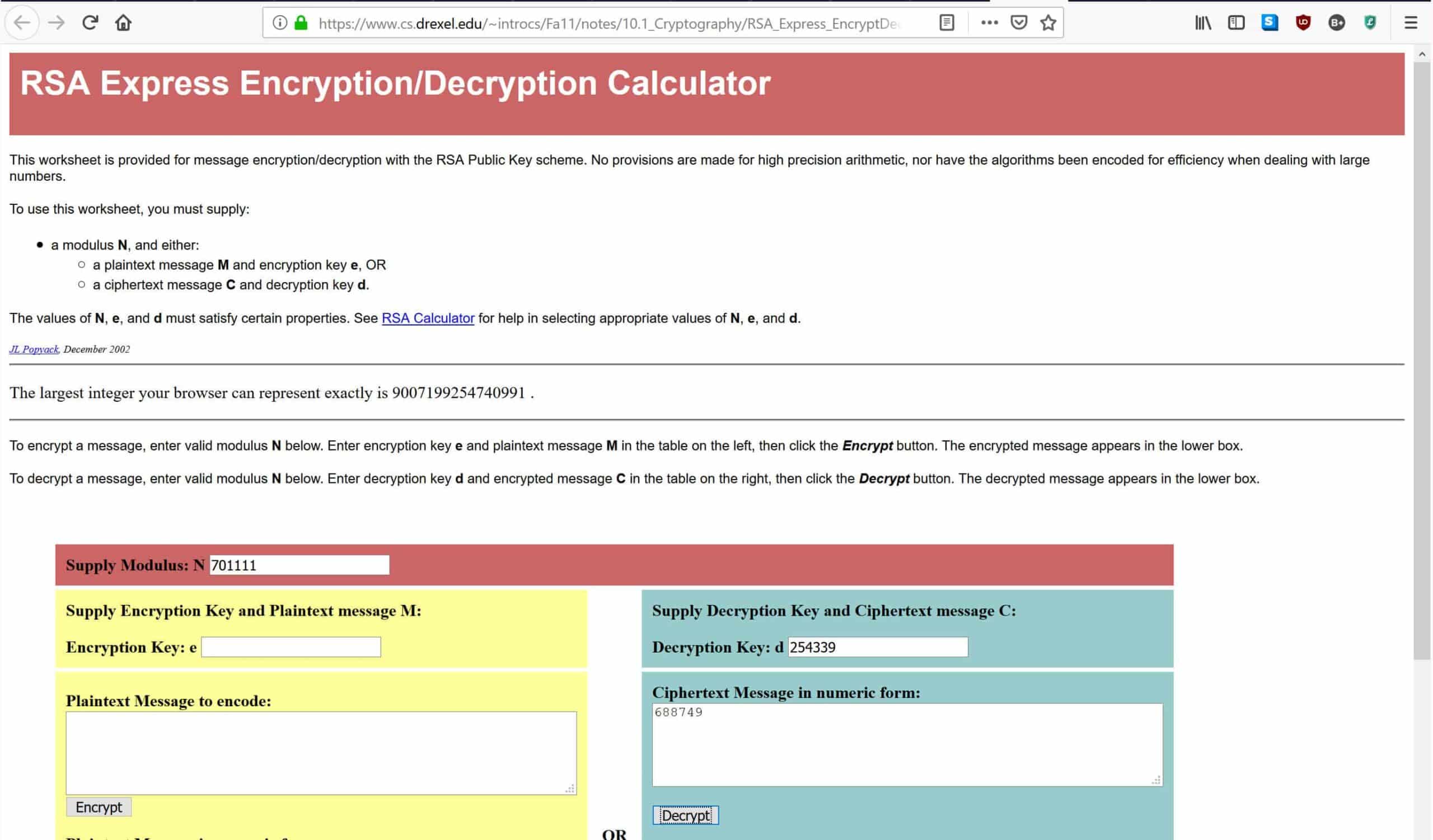
Although you can also select multiple keys in that case all those persons who own those keys will be able to decrypt the message. For this example we will use. To decrypt an enciphered message paste it in the box below enter the key with which it was encrypted in the key box at the top and press the decrypt button.
For this example we will use. There are many packages that include automatic file encryption emails and so on. Software for encryption can typically also perform decryption to make the encrypted information readable again ie.
Wikihowisthebest 4 x research source. To make it unencrypted.